Subscribe to our Telegram channel

Hackers have learned to steal cryptocurrency unnoticed using Avast drivers
Elastic Security Labs together with Antiy specialists have detected a new cryptocurrency mining campaign codenamed REF4578. The GhostEngine malware uses vulnerable drivers to disable antivirus programs and launch the XMRig mining machine.
Elastic Security Labs and Antiy noted the high degree of sophistication of the attack. In their reports, the companies shared threat detection rules to identify and stop such attacks. However, neither report links the activity to known hacker groups or provides details about the victims, so the origin and scale of the campaign remain unknown.
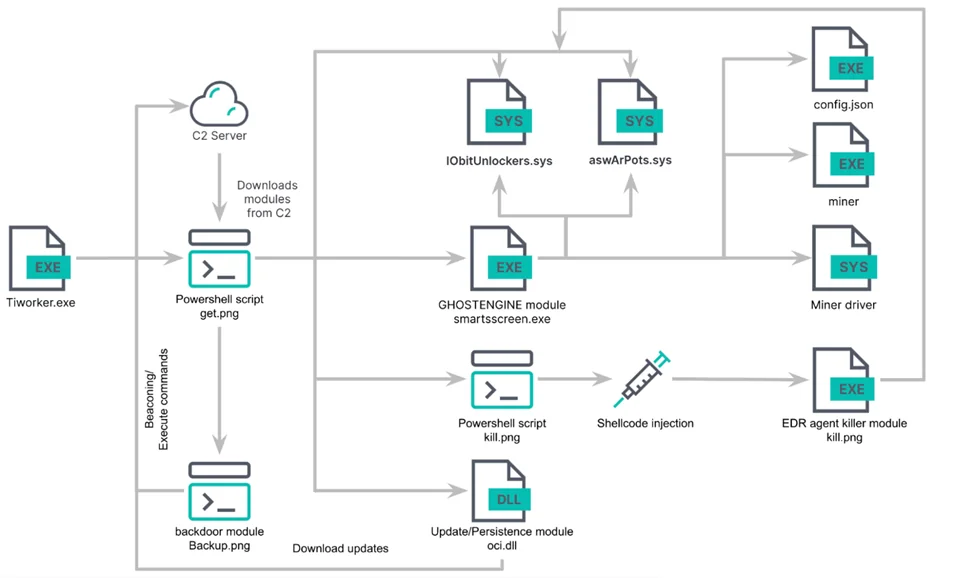
It is unclear how the attackers manage to compromise the servers, but the attack begins with the execution of the Tiworker. exe file, which is disguised as a legitimate Windows file. The executable file is the first stage of the GhostEngine launch, which is a PowerShell script for downloading various modules to the infected device.
Once launched, Tiworker. exe downloads the get. png script from the C2 server, which serves as the main GhostEngine bootloader. The PowerShell script downloads additional modules and their configurations, disables Windows Defender, enables remote services, and clears various Windows event logs.
The script checks for at least 10 MB of free disk space to continue the infection and creates scheduled tasks to ensure the persistence of the threat. The script then downloads and runs the smartsscreen. exe executable file, the main GhostEngine malware. The program disables and removes EDR solutions, as well as downloads and runs XMRig for cryptocurrency mining.
To disable the security programs, GhostEngine downloads 2 vulnerable drivers: aswArPots. sys (Avast driver) to terminate EDR processes and IObitUnlockers. sys (Iobit driver) to remove associated executables.
Elastic experts recommend that users pay attention to suspicious PowerShell executions, unusual process activity, and network traffic indicating cryptocurrency pools. Also, the use of vulnerable drivers and the creation of related kernel services should raise suspicions.
A preventive security measure is to block the creation of files by vulnerable drivers such as aswArPots. sys and IobitUnlockers.sys. Elastic Security also provided YARA rules in its report to help defenders detect GhostEngine infections.
Although the researchers did not find significant amounts on the single payment ID studied, there is a possibility that each affected user has a unique wallet, and the total financial loss could be significant.