Subscribe to our Telegram channel

Co-founder of Ethereum cryptocurrency names the reason for hacking his X-Twitter account
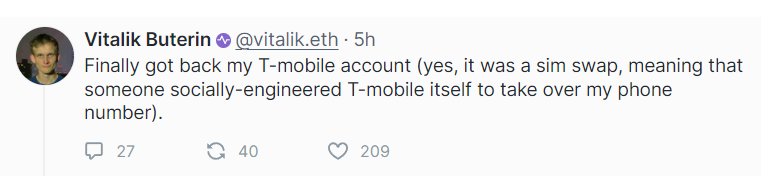
Ethereum co-founder Віталій бутерін" href="https://noworries.media/biography/vitalij-buterin/" data-bio-id="3642">Vitalik Buterin has confirmed that the recent hacking of his Twitter account was a SIM spoofing attack.
During an appearance on Farcaster on September 12, Buterin said that he had finally restored his T-Mobile account after the hacker managed to gain control of it: «Yes, it was a SIM card spoofing, meaning someone socially engineered T-mobile itself to take over my phone number.»
«The phone number is sufficient to reset the password to a Twitter account, even if it is not used as a 2FA [двофакторна автентифікація — ред.],» Buterin noted, adding that users can «completely remove the phone from Twitter.»
«I've seen the advice 'phone numbers are not safe, don’t authenticate with them' before, but I didn’t realize it,» said the father of Ethereum.
As a reminder, on September 9, Buterin’s X account was hijacked by fraudsters who posted a fake NFT distribution. As a result, the victims lost more than $ 691,000.
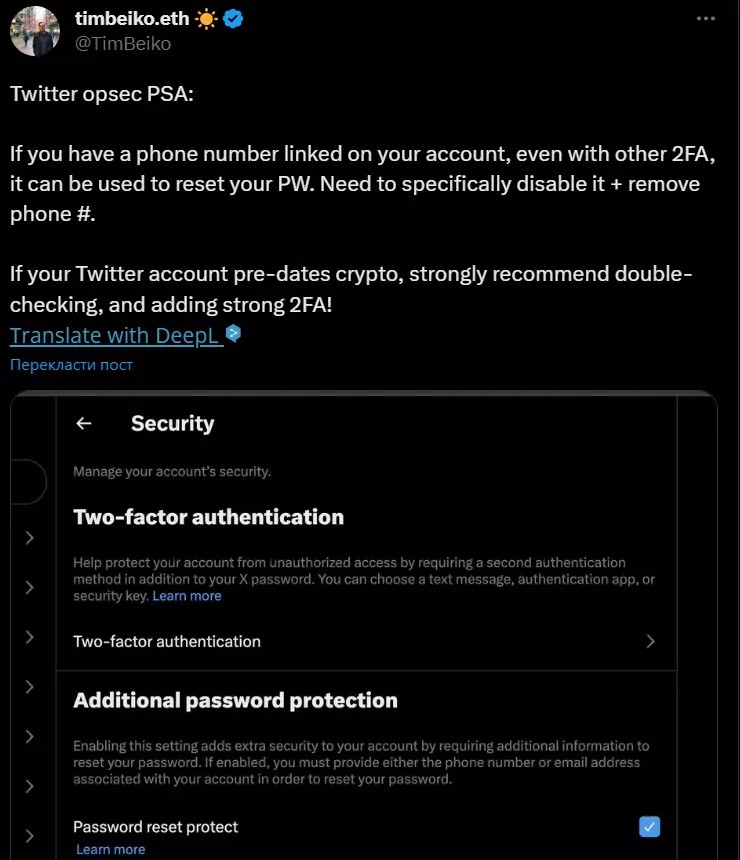
on September 10, Ethereum developer Tim Bako strongly recommended that users remove phone numbers from their X accounts and enable 2FA. «It doesn’t seem difficult to have this feature by default or to enable it by default when an account reaches, say, >10k followers,» he wrote to the platform’s owner Elon Musk.
It should be noted that a SIM spoofing attack or SIM jacking is a method used by hackers to gain control of a victim’s mobile phone number. Fraudsters can use two-factor authentication (2FA) to access social networks, bank and cryptocurrency accounts.